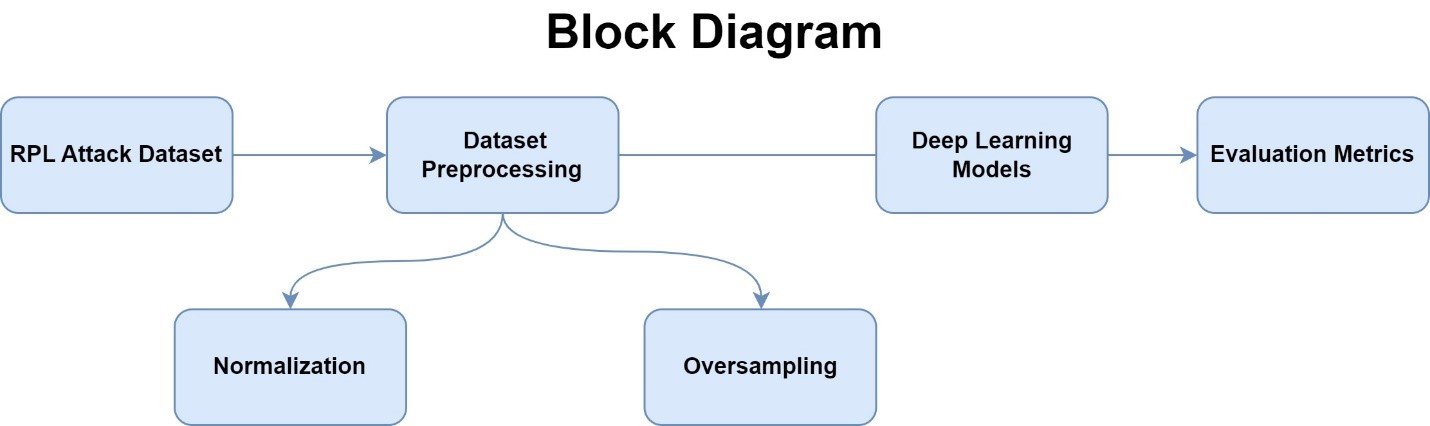
This project aims to classify RPL (Routing Protocol for Low-Power and Lossy Networks) attacks on IoT devices using a hybrid approach combining Long Short-Term Memory (LSTM) and Convolutional Neural Networks (CNN).
The dataset used in this project contains features derived from raw data through simulations conducted using the Contiki Cooja IoT simulator.
These simulations modeled vulnerable IoT environments, focusing on predicting various types of attacks, such as SHA, DFA, SFA, SYA, and VNA.
The dataset was preprocessed and structured for machine learning, capturing key metrics like packet count, source/destination mote ratios, and message counts.
The project is built in Python using TensorFlow, demonstrating a powerful approach to IoT security.
1. Classify RPL attacks on IoT devices using a hybrid LSTM and CNN approach.
2. Train the model to predict different attack types (SHA, DFA, SFA, SYA, and VNA) with high accuracy.
3. Leverage Python and TensorFlow to build and optimize the deep learning model.
4. Utilize a dataset derived from Contiki Cooja IoT simulator simulations, focusing on vulnerable IoT environments.
5. Extract meaningful features such as packet counts, mote ratios, message counts, and durations for attack detection.
6. Improve IoT security by providing an effective method for detecting and classifying RPL-based attacks.
7. Test and validate the model's accuracy and robustness in identifying various attack types in IoT networks.